Being Secure vs Practicing Security,

Risk mitigation is a universal concept that transcends industries, societies applying equally even to life itself. From an evolutionary standpoint, managing risks has been essential for survival, and this principle remains true today across various aspects of life, including those parts that are infused by technology.
This article is the first in a mini series of two articles that explore the need for a fundamental shift in the cybersecurity industry's approach to combating cyber crime. The discussion highlights the limitations of relying solely on advanced tools and tactics, emphasizing that such an approach can only lead to an escalating arms race between defenders and attackers, with no possible resolution. Instead, the focus should be on changing the underlying landscape and mentality, addressing the root causes of cyber crime by focusing on neutralizing cyber criminals, fostering collaboration, and designing user-centric solutions. This strategy could enable an industry-wide transformation that shifts the power and financial advantage from cybercriminals to businesses, paving the way for a more secure and resilient digital environment.
To better understand risk mitigation, let's explore five key strategies and illustrate each with an example:
Risk management is a fundamental concept that applies across various aspects of life, industries, and societies. Along the five strategies outlined above, individuals and organizations must manage and minimize risks, ensuring resilience and adaptability in the face of adversity. There is no other way to survive. It is important to recognize however, that not all of these strategies are built alike and some are more effective than others in providing a state of security.
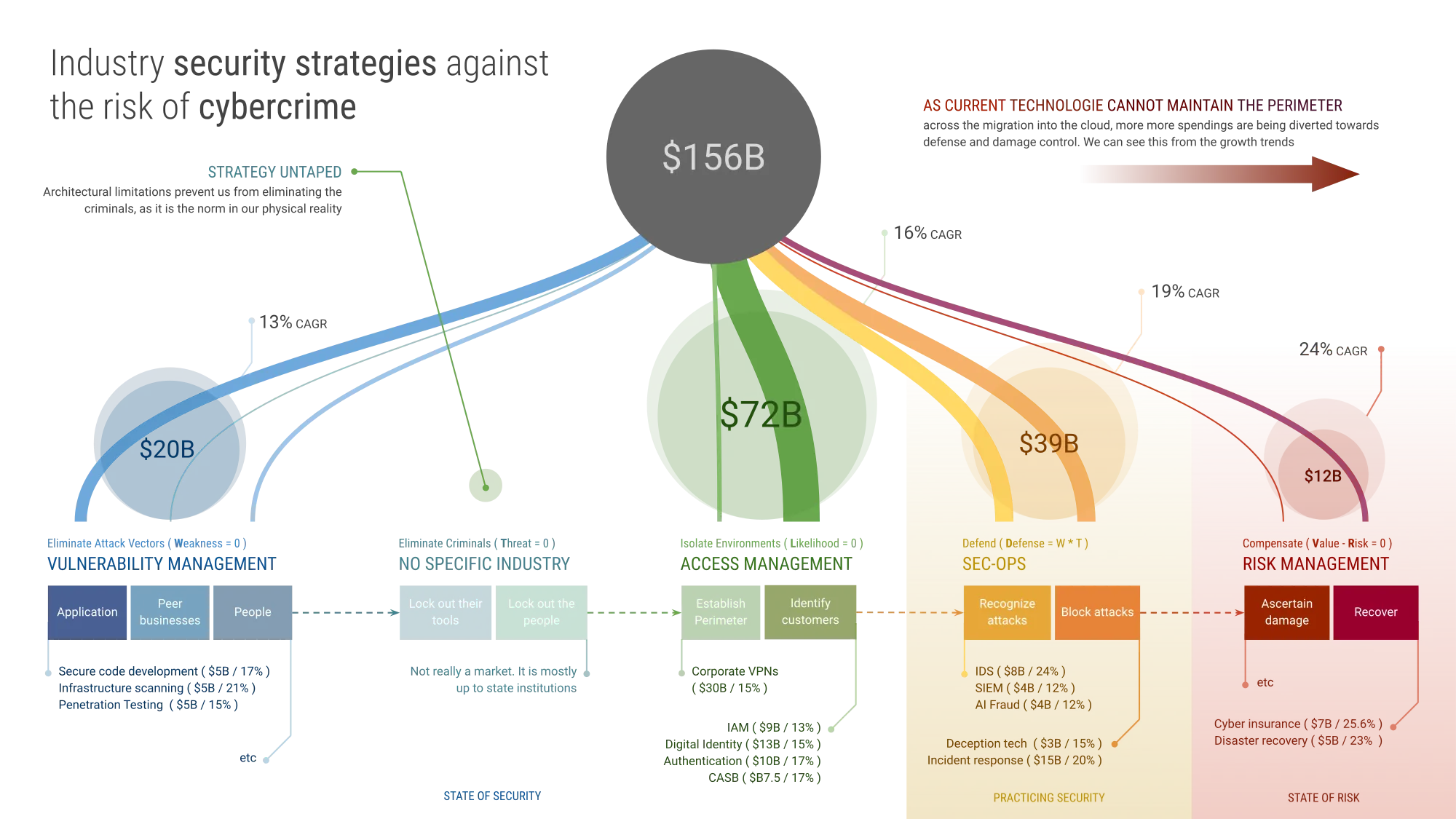
Strategy one, two, and three are preventative measures that aim to minimize risk exposure before an attack or adverse event occurs. These strategies focus on creating a robust defense infrastructure to deter potential threats or diminish their impact. Implementing preventative measures is akin to making a capital investment, where the initial costs can yield long-term benefits, providing protection and security for multiple instances in the future:
Focusing on the above three strategies will result in a state of security - meaning that there isn't any regular chore that needs to be performed to maintain security, security just is. This is what we generally believe to be secure means.
In contrast, strategies four and five are operationally intensive, as they involve dealing with an attack or adverse event in progress or recovering from its aftermath. These strategies can be resource-intensive, time-consuming, and costly, as every investment in operational measures has a limited scope of benefit, typically focused on addressing a single event or issue:
While we consider these two strategies as part of security, they are not in fact able to create a state of security. These strategies only marginally and temporarily maintain security through continuous effort. This is what I call "practicing security", which should definitely not be confused with being in a state of security precisely due to the transient nature of the activity. Failure to allocate the effort or failure of the task itself, will result in immediate demise, so this is in fact from an existential perspective, a state of danger.
Balancing these strategies is essential for effective risk mitigation and resource allocation. In spite of that, in today's cybersecurity landscape, the primary focus is only on four out of the five risk mitigation strategies: elimination of vulnerabilities, access control, defending against attacks, and damage control. The industry generally avoids focusing on the elimination of attackers as a core strategy, largely due to the inherent challenges posed by the design and nature of the internet.
The internet was designed to facilitate communication and information sharing, without any central authority or control. This decentralized structure is a double-edged sword; while it promotes freedom of information, it also makes it difficult to effectively prevent abuse. Cyber criminals can operate from anywhere in the world, often using anonymizing tools and techniques to conceal their identity and location. This makes tracking and neutralizing these individuals or groups a challenging task.
Moreover, the global nature of the internet allows attackers to operate across international borders, further complicating efforts to eliminate them. Jurisdictional issues and differing legal frameworks can hinder cooperation between law enforcement agencies and impede efforts to apprehend cybercriminals.
As a consequence of these challenges, there isn't a specific industry focused solely on the elimination of cyber attackers. Instead, the cybersecurity industry concentrates on developing various techniques along the other four strategies, which are viewed as being more practical and effective in mitigating risks, with more immediate benefits and results to show:
While the elimination of attackers is not a primary focus in the cybersecurity industry, collaboration between private organizations, law enforcement agencies, and governments remains crucial in addressing this challenge. This cooperation does lead to the identification and apprehension of cybercriminals, ultimately contributing to a safer and more secure digital environment, but it is very, very slow and resource intensive, and has a highly accentuated delayed gratification nature. By comparison, logs that show up in intrusion detection systems continuously re-iterate the effectiveness, even though that effectiveness may only be apparent. Equally, when we measure everything in money, it is direct and simple to understand how insurance compensates for lost money, but this does not take into consideration either that not everything can be translated to money, or the long term consequences for letting crime play out. This chase for more immediate rewards skewed the industry away from trying to find mechanisms to stop criminals also, not just crime.
This tendency is clearly visible if we look at the growth pattern of the industries that are aligned with each strategy. Although there is a significant amount of money invested in preventative technologies, businesses are choosing more and more to invest in operational and damage control tools and services. This is a very slippery slope, because the operational strategies are not capitalizing which means that expenses grow, while the security posture does not improve, it's only maintained. With time, aging technologies and strategies create a natural degradation of the state of security, and the negative feedback loop closes in.
This lack of focus on eliminating attackers in the cybersecurity landscape does indeed have a serious downside. By not actively pursuing and neutralizing cyber criminals, the environment inadvertently allows them to adapt, learn, and refine their tactics over time. This can result in an escalating arms race between attackers and defenders, with both sides constantly evolving to outmaneuver each other. As businesses invest in better defenses, criminals learn from their unsuccessful attempts and improve their techniques to bypass these new security measures. This continuous cycle effectively trains cyber criminals, providing them with invaluable experience and knowledge. Each failed attack serves as a lesson, enabling attackers to refine their strategies and develop more sophisticated tools and methods.
A real-world example of this phenomenon is the evolution of ransomware attacks. Initially, ransomware was relatively simple, often involving basic encryption techniques and targeting individual users. As organizations improved their security measures, cyber criminals adapted and began launching more advanced and targeted attacks against businesses and government agencies. The continuous refinement of ransomware tactics, such as double extortion, where attackers both encrypt data and threaten to leak sensitive information, exemplifies the adaptability of cyber criminals in response to evolving defenses.
The consequence of this dynamic is that, eventually, criminals may succeed in breaching even the most secure systems. Driven by this line of thought, organizations must accept that no security system is foolproof, and that the only possible solution is to prepare for the possibility of a successful attack, as famously stated by the former Director of the FBI, Robert S. Mueller, III: "There are only two types of companies - those that have been hacked and those that will be hacked".
Ultimately, the failure to address cyber criminals directly contributes to decreased effectiveness in the cybersecurity industry, pushing it into a more operational mode. As organizations focus on defending against attacks and damage control, they may neglect the root cause of the problem - the attackers themselves. This operational shift comes with several consequences:
***
The current state of the Internet industry is understandably undesirable due to the challenges it faces. In a follow-up article, I will discuss our belief in shifting to a mentality that emphasizes prevention through re-focusing attention towards cyber criminals. By adopting an authenticate-to-connect approach and promoting a secure and collaborative digital ecosystem, the industry can unlock new growth opportunities and avenues. This transformative approach holds the potential to redefine the cybersecurity landscape, leading to a more secure and resilient digital environment for businesses, users, and the wider online community.
LEGAL
Copyright © 2025,
Identity Plus, Inc., New Hampshire, USA,
All rights reserved